The Great Tabletop Hackaton: Shadowrun 1st Edition Play Phase

Run Summary
After deciding on the design parameters for our Shadowrun 1st Edition Matrix run, I got my stopwatch and jumped right into it. I stopped it at the end of every node to keep a running tally of the elapsed time.
Here’s the system map we’re using, for reference:
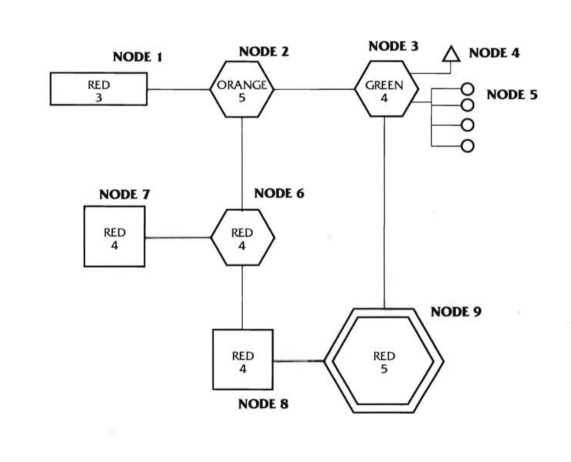
Below is the account of events. As I mentioned before, the actual timed run was written in a brief shorthand and the account below was expanded for readability after the fact.
Node 1 (SAN): Red-3, Trace and Dump-4.
The Decker enters through Node 1, dialing the mainframe’s modem. Security here is unusually tight for a Shadowrun system - the target really doesn’t want anyone sticking their noses in his business.
I hadn’t quite understood the rules here yet, thinking that you couldn’t use your Hacking Pool outside of cybercombat for anything but improvising programs.
So our decker arrives here at Sensor range, improvises Analyze-7 with her pool, and runs that against the ICE, seeing that it’s a potentially dangerous tracer. She moves into Contact range and I roll Initiative even though we’re not in combat, just to have a sense of the flow of the action.
She runs Sleaze against the Tracer using only the program rating, beating the ice but failing anyway because this is a Red node.
From that point on I learn that you can use Hacking Pool dice on any Computer or program test even outside of combat, so I use some on the second attempt and pass even though that has increased difficulty. Ice supressed, we get to whisper “I’m in” into our comms.
And here is where I realize there’s very little reason to be sparing with those pool dice, and that I can use pool dice even for tests with improvised programs. So my strategy for pretty much the rest of the run is to shout I AM SPEED and drop my entire Hacking Pool on any test that doesn’t happen during actual cybercombat.
Total time elapsed so far: 1 turn, 13 minutes.
Node 2 (SPU): Orange-5, Access-6
Another beefy node, and our actual password prompt. Our Decker analyzes the Ice like before, and this fails with a tie. I rule a tie doesn’t activate the ICE. She decides not to try again and just tries Sleaze instead.
I AM SPEED gets us through this just fine - Sleaze works against everything, but Deception would have worked here too. We can see two other nodes from this one, but not what they are. I decide to flip a coin to see where we go next, and we go right towards Node 3.
Total time elapsed so far: 2 turns, 28 minutes.
Node 3: SPU, Green-4, Barrier-3
This is where I arrive at my final interpretation for improvised programs. Improvising them is part of the same action in which you run them, so while this takes only 1 action total, the pool dice you use for the script aren’t available for the test.
Luckily Analyze’s rating doesn’t actually limit what it can discover, so we’re better off improvising an Analyze-1 script and chucking our remaining 13 pool dice into the test than going for Analyze-7 with 1 extra die. Having an actual Analyze program would be even better, but this is pretty good still.
So our reckless Decker successfully analyzes the ICE and Sleazes past it using the same actions and approach as before. I AM SPEED wins again!
She sees there are two connected nodes, and it’s right here that I realize she’s not actually in any danger at Sensor range and can back out after reconnoitering. So Ms. Decker moves into Sensor range of the two connected nodes in order to scout them all and see they’re an I/O Port and a Control node without any ICE in them. She then decides to move on to Node 4.
Total time elapsed: 5 turns, 41 minutes.
Node 4: I/O Port, Green-4.
This node and Node 5 don’t actually have a security rating of their own, so I gave them the same rating as the SPU that was linked to them.
We once again go with I AM SPEED, and our total of 21 dice easily takes care of the system operation needed to disable the camera. Per the rules, after either succeeding at a system operation or giving up after a number of failures, we need to roll a d6. If the result is less than or equal to the number of attempts, the system noticed something wrong and triggered an alert. We only had one attempt before succeeding, and we roll a 3, so no alert.
Camera is off. First goal accomplished!
Total time elapsed: 6 turns, 47 minutes.
Node 5: Control, Green-4.
Same deal as before, and same outcome. Alarm is off, second goal accomplished. And we took less time because I already knew what to do.
Total time elapsed: 7 turns, 50 minutes.
Node 6: SPU, Red-4, Killer-4.
We still have data to steal, so we go to the only unexplored path so far and try to find data stores.
After scouting the node, we follow your usual procedure of Improvised Analyze -> close to Contact range -> Initiative -> Sleaze, always using our whole Hacking Pool for each individual test. We suppress the ICE without issue. If you noticed how reckless we’re being, take a cookie.
Further scouting reviews two data stores attached to this node. I flip another coin to decide where to go, and we go down to Node 8.
Total time elapsed: 10 turns, 58 minutes.
Node 8: Data Store, Red-4, Black Ice-5.
Our usual Improvised Analyze routine shows us this data store is protected by Black Ice! This is scary, but is also a very promising lead.
Disregarding the danger, our Decker goes all in and chucks her whole Hacking Pool into Sleaze again. She succeeds by exactly the needed amount and suppresses the ice.
She then uses Browse to find any drainable accounts, because she doesn’t know the full layout of the system like we do. The operation succeeds but she doesn’t find anything. Boo!
Remembering the actual mission, she Browses for incriminating evidence and finds it. She has enough disk space for the file, and no time pressure for the download, so we just wait a couple more turns. Third objective accomplished!
She still wants to find that money, though, so she moves to the other data store at Node 7.
Total time elapsed: 13 turns, 1 hour, 9 minutes.
Node 7: Data Store, Red-4, Access-5
Same deal as usual. Improv Analyze reveals the ICE, Sleaze gets past it, Browse confirms there’s nothing of value to the team in this node.
Here is where I begin to notice that despite the different types of nodes and the flowery descriptions of virtual dungeons, we’ve been performing more or less the same sequence of tests in the same order, in a loop. So I guess a long enough Matrix run might seem a bit boring for the decker as well. I’m still having fun here, because lucky rolls have given me a string of successes, but I don’t feel like I’m in danger or having to make complex decisions.
Anyway, the only unexplored node left is the CPU. A cautious decker might decide to cut their losses, perform the single remaining system operation they need, and jack out. But we’ve already established our Decker is not cautious, SHE IS SPEED!
Total elapsed time: 14 turns, 1 hour, 20 minutes.
Node 9: CPU, Red-5, Trace and Burn-6, Black Ice-4
The setup is a little unusual here. This CPU has all the standard system operations available, and the Trace and Burn-6 is protecting those. It also has a link to the target’s bank account, and draining it counts as a custom system operation. There’s a piece of Black Ice protecting that operation only.
So our Decker will have the run of the system if she neutralizes the Tracer, but to get the money she must also get past the Black Ice.
She comes within Sensor Range, Improv-Analyzes both pieces of Ice, and sees what they’re protecting. She decides to deal with the Tracer first. I roll Initiative for everyone as she gets into Contact Range, but the ICE will only act if it activates.
Despite the usual I AM SPEED approach giving us 19 dice to Sleaze past the Tracer, the node’s high security level prevents us from succeeding. We try again with increased difficulty, and this time a very unlucky roll gives the ice more successes, meaning it activates!
The first thing Trace and Burn does upon activation is try to raise an Internal Alert in the system. This causes the ratings of all ICE to increase by 50%, so we’re actually dealing with Trace-and-Burn 9 now. The Black Ice also improves to Rating 6, but it remains inactive since it’s only protecting the bank account.
We could have allocated dice from our Hacking Pool to an opposed test to “jam” the ice and prevent the alert from going through… but we already used all of them on the Sleaze attempt, and the pool hasn’t refreshed yet. This is why our Decker has been very reckless so far, as every piece of ice she faced until now could have done this on a failed test.
On its first actual action, Trace and Burn rolls its rating to determine how long it will take to trace the Decker. We’re lucky here because this roll gets only 1 success, meaning it will take a total of 10 of the IC’s actions to do so. Once that time is up, though, her deck is toast.
Our Decker switches to using the Attack program to destroy the Tracer before that happens. This is proper cybercombat, which works a little differently. The “to-hit” roll is an unopposed test with only with your Hacking Pool against the Node’s security. The program’s rating is your base damage if you hit, and it increases by 1 for every extra success past the minimum required to hit. Actual damage is your net successes in an opposed test of the ICE’s rating versus your damage pool.
I end up using my entire pool in the to-hit roll, since any less than that means I won’t be beating the difficulty on average. It takes me 3 turns to destroy the Tracer this way, but since everyone acts multiple times per turn I only had 3 actions left before the trace completed. This was still somewhat repetitive since it was the same set of rolls every time, but it was also exciting since this is the first time our Decker is in any actual danger.
With the tracer gone, she uses a system operation to cancel the alert and manages to Sleaze past the Black Ice and drain the target’s account. Bonus objective completed!
With that done, she moves normally to the Control Modules and opens the final door, completing the mission’s objective. She then jacks out. Mission Complete!
Total time elapsed: 19 turns, 2 hours and 4 minutes. This combat alone took 41 minutes to resolve.
Run Analysis and Impressions
I’m not gonna lie, I kinda feel like I completed an important life goal. I could never understand this hacking system when I was 12, but now not only did I grok it, I finished an entire Matrix run while using it. So I’m pretty happy, and I had fun.
However, I must also conclude that all the criticisms leveled at this system are valid.
As mentioned in the intro, we’re assuming our physical team has an easy time getting past the reception area. This would take some light roleplaying and a roll or two from our talker. That plus walking to the restricted area might take 10 minutes of real time, but it takes the decker 50 minutes to complete the goals that let them move forward from there.
The next part of the physical mission will involve more tests and die rolls from the physical team. The Decker takes around half an hour of real time to find the electronic evidence, and it might be accurate to assume the physical team takes about the same or a little bit longer to sneak past the guards and find the physical documents. Let’s say 40 minutes for the physical team.
Then the Decker decides to loot the server, and that takes 41 minutes. Unless the physical team is having an epic shootout at the same time as they try to leave the building, all they have to do is sit and wait. Otherwise they take maybe 10 minutes total to reach the back door and walk out.
So a team that has a firefight on the way out might take up 90 minutes of real time, and a team that doesn’t will take perhaps 50 with their part of the mission. Our Decker is taking up at best over half and at worst over two-thirds of the session with her solo VR dungeon crawl. And this is all assuming a 100% buttery smooth session with absolutely no digressions, distractions, or rule arguments to make it longer.
There was also a point where I kinda felt that the decking run itself was getting a little repetitive, because the “optimal” procedure to follow became obvious: Improv Analyze -> Sleaze, always dumping the entire Hacking Pool into each test. In actual cybercombat, I also ended up doing the same thing over and over until the enemy died. It was still enjoyable, but I could see it eventually overstaying its welcome even for the decker player.
Finally, if it turns out that my rules interpretations were overly generous and this was supposed to be way harder, then all the criticisms I made become even stronger, because everything would take more time and more rolls.