The Great Tabletop Hackaton: Cyberpunk 2020

For this post, we’ll be using Cyberpunk 2020 Version 2.01, published in 1993 if I understood the copyright notice correctly. The original edition of Cyberpunk was from 1988. Cyberpunk 2020 came out in 1990, and this version only adds minor corrections on top of that. I’m given to understand the rules themselves didn’t change much from the original edition.
I used to own a physical copy of this corebook back when I was a teenager, so I also get a bit of cozy nostalgia for looking at the PDF of it now, but I would definitely not play it as written today.
Setting Overview
The setting’s global network is called the Net, or sometimes the NET in all caps. I’ve heard claims that it doesn’t take inspiration from Neuromancer, but the description I’m reading here leans as much into Neuromancer imagery as Shadowrun’s.
Hacker characters are called Netrunners, and they use devices called cyberdecks that range from the size of a desktop workstation to the size of a paperback book, with a lot of plugs for neural interfaces and data lines but no built-in keyboard or monitor. Decks all have the same starting stats, but smaller and more portable models are more expensive. The most expensive deck is the only one that has a built-in cellular modem. All the others need to jack into landlines or directly into target devices.
The most expensive decks are cheaper than a subcompact car, and they get much more affordable if you give up that cellular modem. However netrunners are still a specialized niche because Cyberpunk 2020 is a class-based system. Netrunner is a specific class (or “Role”), and only they get the Interface skill that’s used for hacking.
While Shadowrun’s Matrix uses mainframes as the “backing” for its sci-fi chrome flash, behind CP 2020’s flash is yet more flash with a dash of space magic. The overall Net still works kinda like a phone grid, but the book works very hard to make the reader see it as, effectively, a parallel dimension. Back in 2014 some researchers effectively cast a spell over the telecom grid and turned it into a “conceptual space” where each phone line and connected device is located in a point analogous to its physical location. When you connect to the Net you form an “ICON” (all caps) representing yourself at the point of entry, and accessing other servers means making that ICON actually travel the distance between its entry point and the destination. If you’re in Night City and your destination is in Japan, there’s no way to reach it except hopping into a Long Distance Link and flying over the entire Pacific Ocean.
There are serious musings about how the “empty space” you fly over while traversing these links is teeming with unindentified greeblies because every computer is on the Net by simply being turned on. If it doesn’t have a connection, it’s still on the Net, it’s just unreachable from the telecom grid. Adding new connected systems “physically increases” the size of the Net, and you could extend it to space by launching a server in a spaceship.
Mechanics Overview
There is a lot of talk about local and regional telecom grids, much like in Shadowrun, and a big emphasis on paying your phone bill for your home landline or cellular modem, because CP 2020 never loses an opportunity to joke about militarized debt collection squads.
The main reasons to run the Net are to provide support to a physical team, and to recover data from a target server. We can surprisingly already see the image of the netrunner who stays together with their team here and hacks a series of remotely controlled devices, doing stuff like controlling robot cars or opening doors without having to do a full run. However only some PCs will be able to do this out of the gate, since they might not have the cash for that cellular portable deck. Oh, and this is an 80s cell, so moving too fast will break your link. No 5G for you!
For those who can, there’s a series of control programs designed for different types of device. Anything that can be described as “computer controlled” can be hacked this way if the PC has the appropriate program, since due to SPACE MAGIC, everything computerized is automatically in the Net. There are also programs for remaining hidden, getting past barriers, and attacking both other programs and other people. Everyone is going to want these even if they’re using a desktop.
The netrunner’s Interface class skill is required to run the Net at all, but is not used for all netrunning tasks. Its main use is in combat against security programs (IC, “ice”) or other netrunners. Due to the way the character creation system works it also determines your starting money.
The kind of server you expect a netrunner to hack is called a Data Fortress. It vaguely resembles a mainframe, but as the name implies it goes all in on the VR Dungeon aesthetic, even harder than Shadowrun did. You’re not moving through an abstract representation of a mainframe, you’re crawling an actual dungeon-like structure drawn on a 10x10 square grid. It has walls, gates, and security programs acting like wandering monsters, and memory banks that work like treasure chests. They have CPUs that act like brains, and give them an INT score and possibly skills that are useful both in its day-to-day operations and when fighting netrunners. A Fortress with an INT of 12 or higher (which requires 4 CPUs) is a sapient AI and has a personality.
Security programs are drawn from the same master list as netrunner programs. You place them like monsters in the dungeon.
Run Parameters
Sadly CP 2020 does not include sample characters, so we have to create one. We’ll also need to create our target system, because the example there is a bit too high level for us.
Our Netrunner: G0blin
So called because of his looks, he prefers to work from home.
I’m using my Cyberware Capacity rules instead of Humanity, but that’s the only tweak I did here. I lucked out on the starting stat and cash rolls and decided to optimize my money by getting a desktop with expanded memory instead of a portable deck.
INT 10 REF 9 TECH 7 LUCK 6 EMP 6 MA 5 COOL 4 BODY 4 ATTR 3
Cyberware Capacity: 11/40.
Career Skills
- Interface - 8
- Awareness/Notice - 5
- Basic Tech - 4
- Education - 3
- System Knowledge - 4
- CyberTech - 2
- Cyberdeck Design - 4
- Composition - 1
- Electronics - 4
- Programming - 5
Pickup Skills
Handguns 6, Stealth 6, Persuasion 1
Cyberware
- Neural Processor (1k, CC 6),
- Cybermodem Link (100, CC 1),
- Interface Plugs (200, CC 4)
Equipment
- Desktop deck (20 MU, Speed 0, Data Wall 2, 6k)
- Killer 6 (STR 6, 5 MU, 1480 eb),
- Stealth (STR 4, 3 MU, 480)
- Wizard’s Book (STR 6, 2 MU, 400 eb)
- Crystal Ball (STR 4, 1 MU, 140 eb)
- Genie (STR 5, 1 MU, 150 eb)
Our System
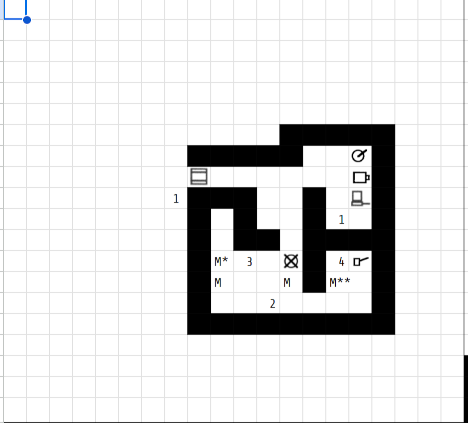
By following the rules in the CP2020 core book, and with a little help from its random generation system, I came up with the Data Fortress depicted above.
Here’s the key to the numbers and symbols in the file:
- 1: Watchdog
- 2: Bloodhound
- 3: Stun
- 4: Knockout
- M*: Financial File, where the money is.
- M**: Grey Ops file, where the evidence is.
That Knockout was a originally a Hellhound, but I thought that might be a bit excessive since the book keeps describing it as the scariest thing ever, only employed by the richest and nastiest corporations. Still, there’s not much difference for us, as one hit from the Knockout will still ensure a mission failure.
Run Summary
G0blin arrived from the left side of the screen. The Watchdog next to the gate spotted him when he got close despite the running Stealth program. He destroyed it with one attack, and then proceeded to crack the gate. Inside, he first went right to the remotes and got spotted by another Watchdog. As before, he won initiative and destroyed it with one attack.
Then he moved down, clipping through the CPU. He managed to stay hidden from both the Bloodhound and the much more dangerous Stun, bushwhacking them with sneak attacks. He examined the data stores there and drained the company’s accounts.
Then he went into the little corner room for the final leg of the mission. The Knockout program didn’t spot him at first, but also didn’t go down with the sneak attack. They went to initiative, G0blin won, and finished the program off. This left him free to finish the mission, as both the door and evidence were right there.
The run succeeded and took a total of around 21 game turns and 32 minutes of real time.
Run Analysis and Impressions
I found this less enjoyable than Shadowrun’s system, I guess, but it’s mostly because of me. I’m not a big fan of how this game views the Net, or of how much a net run resembles a roguelike dungeon crawl. Nevertheless it was faster.
I do wonder if the quick runtime might have been because this host was too easy. How would it have gone if I used the Militech regional office that comes as an example as my system for this run? Or maybe I got something wrong when designing the fortress or running the session?
Let’s assume I got things right and the physical team takes the same amount of time from the SR1 post to do their part (50 minutes for a perfectly stealthy run or 90 for one with a firefight). This means the hacker takes up anywhere from a third to half the session. That’s still more than the theoretic “ideal” ratio of 25%, but perhaps it could be alleviated with a bit of proper scene management.
As far as VR dungeon crawls go, CP 2020’s are much more like brutal raids than Shadowrun’s careful sneaking missions. Non-combat programs add only their Strength to the d10 roll, while attacks and defenses use the netrunner’s INT and Interface skill as well. Attacks are also much more devastating, since most programs have a Strength of less than 6, and that 1d6 damage Killer programs do reduces Strength directly. Even if the target survives, it’s greatly weakened.
On the other hand, if any of those anti-personnel programs had managed to act and hit our runner, they’d instantly be put out of commission and the mission would fail. That’s another way in which it resembles a roguelike: the key to victory is to bump the monster before the monster bumps you.
There were several things that were unclear to me here:
Do detection rolls happen only once, or do they happen every turn? I went with “every turn”, and this ended up making things more violent. Most ICE that initially missed G0blin ended up spotting him on the second roll and forcing him to enter combat.
Do you need control programs to operate those remote icons from a data fortress? I went with “no” despite buying a couple of those for G0blin, because the examples were all about netrunners controlling physical objects close to them from meatspace. If I had went with “yes”, it would only have increased the amount of turns the run took by a bit, since G0blin only tried to control these remotes when all neighboring ICE had been killed.
I also didn’t know what happened when a Watchdog spotted G0blin. Text said it “alerts its owner”, but does that happen immediately or does the dog have to run to where the owner is? I judged the program had to travel to the owner since the setting places so much emphasis on the “physicality” of the Net. That would be the terminal icon here in our map, but no dog ever made it there. If any had, we might have seen an enemy netrunner here and the run would have perhaps been harder.